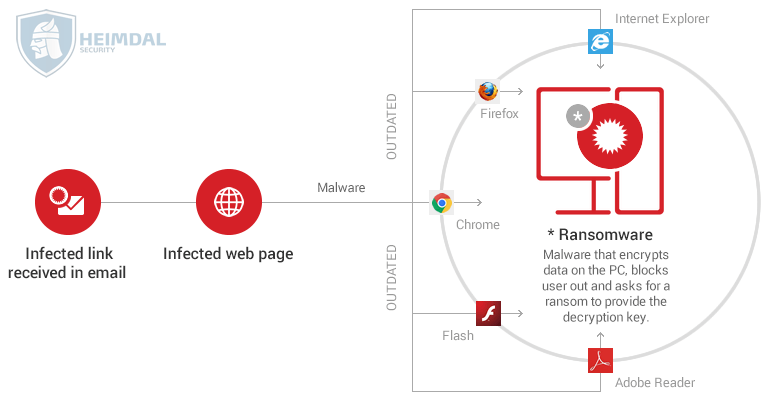
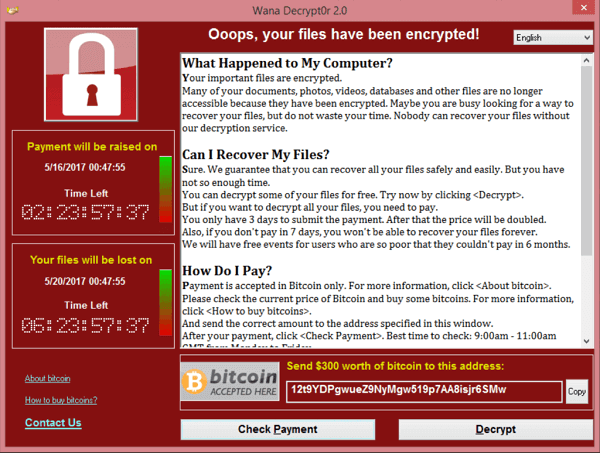
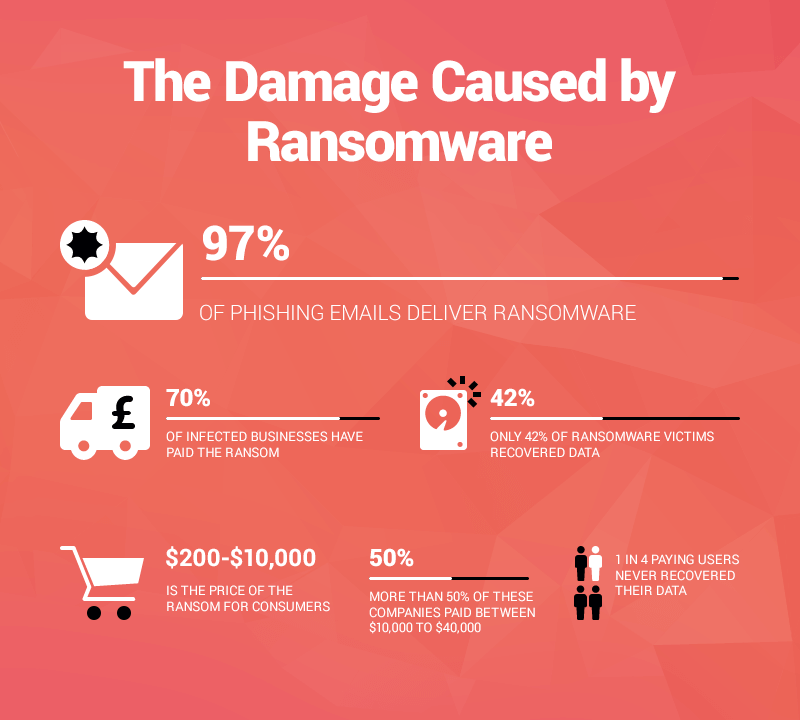
The emerging world of
information technology is one in which data is king, social platforms evolve as
a new source of business intelligence, and cloud computing finally delivers on
IT’s role as a driver of business growth, according to a new report from Accenture
(NYSE: ACN).
The Accenture
Technology Vision 2011 identifies eight emerging trends that challenge
long-held assumptions about IT and are poised to reshape the business
landscape. The report also offers “action steps” that high performing businesses
and governments can take to prepare for the new world of computing.
1) Platform
Architecture
One of the most
significant trends identified in the report finds that the age of “viewing
everything through an application lens is coming to an end.” Instead, platform
architectures will be selected primarily to cope with soaring volumes of data
and the complexity of data management, not for their ability to support
applications.
The tried and true
relational database will not go away, but it will soon start to make way for
other types of databases – streaming databases, for instance – that mark a
significant departure from what IT departments and business users have relied
on for decades.
2) Social Platforms
The report also
predicts the evolution of social media into social platforms. This means
company websites may no longer be the first port of call for customers. This
has the potential to disrupt the way companies conduct business, posing new
challenges – and opportunities – for IT.
For example, “social
identities” – based on the rich history of information that individuals leave
in social networks – will become much more valuable to businesses than the
traditional and isolated information they get when an individual registers on
their corporate website.
3) Cloud Computing
Accenture also sees a
new conversation emerging around cloud computing, which will become so
pervasive that the term itself becomes superfluous. According to the report,
hybrid clouds – software-as-a-service (SaaS) and platform-as-a-service (PaaS)
in combination with internal applications – will “cement IT’s role as a driver
of business growth.”
The focus will shift
from simple infrastructure solutions to developing cloud strategies that
deliver increased functionality and flexibility using a mix of public and
private cloud-based application and platform services. While many challenges
remain, cloud is nonetheless poised to change the face of enterprise computing.
4) Data Security
The fortress mentality,
in which all IT has to be architect ed to be foolproof, is giving way
to a security architecture that responds proportionately to threats when
and where they happen.” As a result, the role of people in data security will
decline, replaced by automated capabilities that detect, assess, and respond
immediately.
5) Data Privacy
Individual privacy will
take center stage as a result of increased government regulation and policy
enforcement. The report concludes: “We expect that leading players will develop
superior levels of understanding, enterprise-wide, about the distinctions between
being a data processor – broadly handling the personal data of others – versus
being a data controller, thus lowering the risks of unwitting breaches or
privacy regulations and perceptions of privacy breakdowns.”
6) Analytics
Companies that continue
to view analytics as a simple extension of business intelligence will be
“severely underestimating analytics’ potential to move the needles on the
business.” Among other failings, traditional BI does not take advantage of the
wealth of unstructured data that is now available. IT leaders will need to work
closely with business leaders to identify where analytics can be leveraged
effectively, as well as the proper mix of services required to optimize
analytics capabilities across the enterprise.
7) Architecture
Information technology
is evolving from a world that is server-centric to one that is service-centric.
Companies are quickly moving away from monolithic systems that were wedded to
one or more servers toward finer-grained, reusable services distributed inside
and outside the enterprise. The goal: to decouple infrastructure, systems,
applications, and business processes from one another.
8) User Experience
Today, business process
design is driven by the need for optimization and cost reduction. Tomorrow it
will be driven by the need to create superior user experiences that help to
boost customer satisfaction. Great user experiences will require more layered
approaches than what is typical today. As such, application design will be a
multidisciplinary exercise: Typically handled today by IT architects and
business owners, tomorrow it will involve optimization from the perspective of
the process actor, with the emphasis on simplicity and on removing
inefficiencies.