May 12th 2017 saw the biggest ever cyber attack in Internet history (yes, bigger than the Dyn DDoS). A ransomware named WannaCry stormed through the web, with the damage epicenter being in Europe.
What is Ransomware?
Ransomware is a sophisticated piece of malware that blocks the victim’s access to his/her files, and the only way to regain access to the files is to pay a ransom.
There are two types of ransomware in circulation:
Encryptors, which incorporates advanced encryption algorithms. It’s designed to block system files and demand payment to provide the victim with the key that can decrypt the blocked content. Examples include CryptoLocker, Locky, CrytpoWall and more.Lockers, which locks the victim out of the operating system, making it impossible to access the desktop and any apps or files. The files are not encrypted in this case, but the attackers still ask for a ransom to unlock the infected computer. Examples include the police-themed ransomware or Winlocker.Some locker versions infect theMaster Boot Record (MBR). The MBR is the section of a PC’s hard drive which enables the operating system to boot up. When MBR ransomware strikes, the boot process can’t complete as usual and prompts a ransom note to be displayed on the screen. Examples include Satana and Petya families.
Crypto-ransomware, as encryptors are usually known, are the most widespread ones, and also the subject of this article. The cyber security community agrees that this is the most prominent and worrisome cyber threat of the moment.
Crypto-ransomware, as encryptors are usually known, are the most widespread ones, and also the subject of this article. The cyber security community agrees that this is the most prominent and worrisome cyber threat of the moment.
Ransomware has some key characteristics that set it apart from other malware:
- It feature sunbreakable encryption, which means that you can’t decrypt the files on your own.
- It has the ability to encrypt all kinds of files, from documents to pictures, videos, audio files and other things you may have on your PC;
- It can scramble your file names, so you can’t know which data was affected. This is one of the social engineering tricks used to confuse and coerce victims into paying the ransom;
- It will add a different extension to your files, to sometimes signal a specific type of ransomware strain;
- It will display an image or a message that lets you know your data has been encrypted and that you have to pay a specific sum of money to get it back;
- It requests payment in Bitcoins because this crypto-currency cannot be tracked by cyber security researchers or law enforcements agencies;
- Usually, the ransom payments have a time-limit, to add another level of psychological constraint to this extortion scheme. Going over the deadline typically means that the ransom will increase, but it can also mean that the data will be destroyed and lost forever.
- It uses a complex set of evasion techniques to go undetected by traditional antivirus (more on this in the “Why ransomware often goes undetected by antivirus” section);
- It often recruits the infected PCs into botnets, so cyber criminals can expand their infrastructure and fuel future attacks;
- It can spread to other PCs connected to a local network, creating further damage;
- It frequently features data exfiltration capabilities, which means that it can also extract data from the affected computer (usernames, passwords, email addresses, etc.) and send it to a server controlled by cyber criminals; encrypting files isn’t always the endgame.
- It sometimes includes geographical targeting, meaning the ransom note is translated into the victim’s language, to increase the chances for the ransom to be paid.
Ransomware is here to stay. The current conditions are a perfect storm which makes it the easiest and viable source of money for any malicious hacker out there:
- Ransomware-as-a-service, where malware creators sell its services in exchange for a cut in the profits.
- Anonymous payment methods, such as Bitcoin, that allow cybercriminals to obtain ransom money knowing their identity can’t be easily revealed.
- It’s impossible to make a completely secure software program. Each and every program has its weaknesses, and these can be exploited to deliver ransomware, as was the case with WannaCry.
- The number of infections would drastically shrink if all users were vigilant. But most people aren’t, and they end up clicking infected links and other malicious sources.
Why ransomware creators and distributors target home users:
- Because they don’t have data backups;
- Because they have little or no cyber security education, which means they’ll click on almost anything;
- Because the same lack of online safety awareness makes them prone to manipulation by cyber attackers;
- Because they lack even baseline cyber protection;
- Because they don’t keep their software up to date (even if specialists always nag them to);
- Because they fail to invest in need-to-have cyber security solutions;
- Because they often rely on luck to keep them safe online (I can’t tell you how many times I’ve heard “it can’t happen to me”);
- Because most home users still rely exclusively on antivirus to protect them from all threats, which is frequently ineffective in spotting and stopping ransomware;
- Because of the sheer volume of Internet users that can become potential victims (more infected PCs = more money).
Why ransomware creators and distributors target businesses:
- Because that’s where the money is;
- Because attackers know that a successful infection can cause major business disruptions, which will increase their chances of getting paid;
- Because computer systems in companies are often complex and prone to vulnerabilities that can be exploited through technical means;
- Because the human factor is still a huge liability which can also be exploited, but through social engineering tactics;
- Because ransomware can affect not only computers but also servers and cloud-based file-sharing systems, going deep into a business’s core;
- Because cyber criminals know that business would rather not report an infection for fear or legal consequences and brand damage.
- Because small businesses are often unprepared to deal with advanced cyber attacks and have a relaxed BYOD (bring your own device) policy.
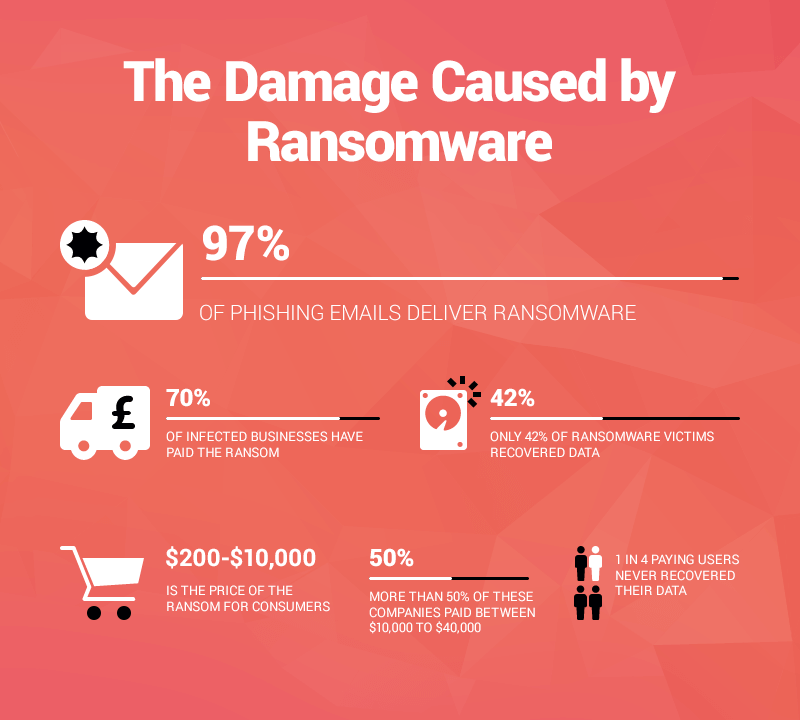
Why ransomware creators and distributors target public institutions:
- Because public institutions, such as government agencies, manage huge databases of personal and confidential information that cyber criminals can sell;
- Because budget cuts and mismanagement frequently impact the cybersecurity departments.
- Because the staff is not trained to spot and avoid cyber attacks (malware frequently uses social engineering tactics to exploit human naivety and psychological weaknesses);
- Because public institutions often use outdated software and equipment, which means that their computer systems are packed with security holes just begging to be exploited;
- Because a successful infection has a big impact on conducting usual activities, causing huge disruptions;
- Because successfully attacking public institutions feeds the cyber criminals’ egos (they may want money above all else, but they won’t hesitate to reinforce their position in the community about attacking a high-profile target).
In terms of platforms and devices, ransomware doesn’t discriminate either. We have versions tailor-made for personal computers (too many types to count, but more on that in “Notorious families” section), mobile devices (with Android as the main victim and a staggering growth) and servers.
Will continue on Ransomware, its infectious and its precautions in the next blog. Please be updated.


No comments:
Post a Comment