When it comes to servers, the attack is downright vicious:
Some groups do this by infiltrating the target server and patching the software so that the stored data is in an encrypted format where only the cybercriminals have the key to decrypt the data.
The premise of this attack is to silently encrypt all data held on a critical server, along with all of the backups of the data.
This process may take some time, depending on the organization, so it requires patience for the cybercriminals to carry it out successfully.
Once a suitable number of backups are encrypted, the cybercriminals remove the decryption key and then make their ransom demands known, which could be in the order of tens of thousands of dollars.
How do ransomware threats spread?
Cyber criminals simply look for the easiest way to infect a system or network and use that backdoor to spread the malicious content.
Nevertheless, these are the most common infection methods used by cybercriminals
- Spam email campaigns that contain malicious links or attachments (there are plenty of forms that malware can use for disguise on the web);
- Security exploits in vulnerable software;
- Internet traffic redirects to malicious websites;
- Legitimate websites that have malicious code injected in their web pages;
- Drive-by downloads;
- Malvertising campaigns;
- SMS messages (when targeting mobile devices);
- Botnets;
- Self-propagation (spreading from one infected computer to another); WannaCry, for instance, used an exploit kit that scanned a user’s PC, looking for a certain vulnerability, and then launched a ransomware attack that targeted it.
- Affiliate schemes in ransomware-as-a-service. Basically, the developer behind the ransomware earns a cut of the profits each time a user pays the ransom.
Crypto-ransomware attacks employ a subtle mix of technology and psychological manipulation (also known as social engineering).
These attacks get more refined by the day, as cyber criminals learn from their mistakes and tweak their malicious code to be stronger, more intrusive and better suited to avoid cyber security solutions. The WannaCry attack is a perfect example of this since it used a wide-spread Windows vulnerability to infect a computer with basically no user interaction.
That’s why each new variant is a bit different from its forerunner. Malware creators incorporate new evasion tactics and pack their “product” with piercing exploit kits, pre-coded software vulnerabilities to target and more.
How do ransomware infections happen?
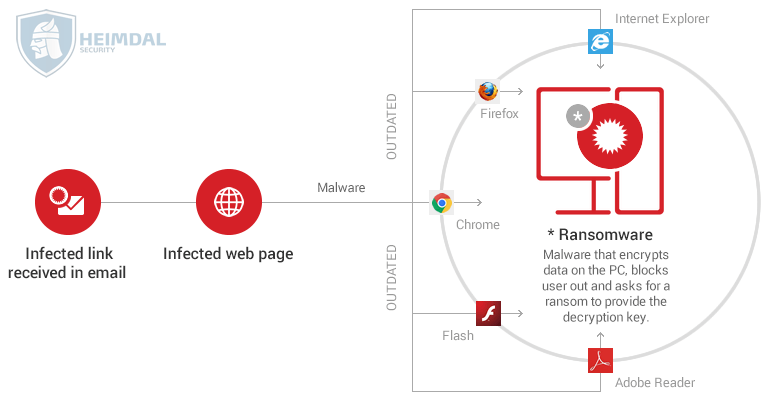
- Initially, the victim receives an email which includes a malicious link or a malware-laden attachment. Alternatively, the infection can originate from a malicious website that delivers a security exploit to create a backdoor on the victim’s PC by using a vulnerable software from the system.
- If the victim clicks on the link or downloads and opens the attachment, a downloader (payload) will be placed on the affected PC.
- The downloader uses a list of domains or C&C servers controlled by cyber criminals to download the ransomware program on the system.
- The contacted C&C server responds by sending back the requested data.
- The malware then encrypts the entire hard disk content, personal files, and sensitive information. Everything, including data stored in cloud accounts (Google Drive, Dropbox) synced on the PC. It can also encrypt data on other computers connected to the local network.
- A warning pops up on the screen with instructions on how to pay for the decryption key.
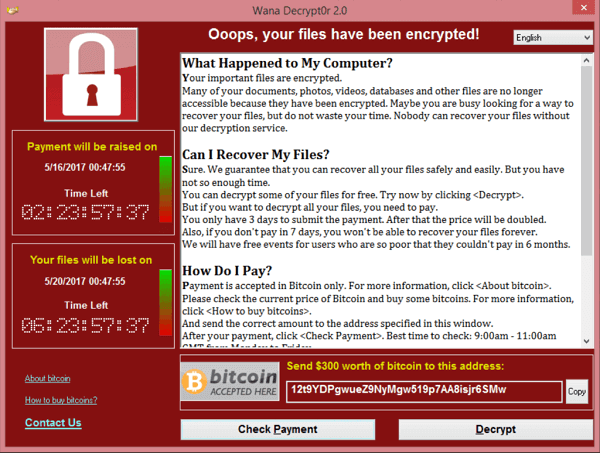
Everything happens in just a few seconds, so victims are completely dumbstruck as they stare at the ransom note in disbelief.
Ransomware uses several evasion tactics that keep it hidden and allow it to:
- Not get picked up by antivirus products
- Not get discovered by cyber security researchers
- Not get observed by law enforcement agencies and their own malware researchers.
The rationale is simple: the longer a malware infection can persist on a compromised PC, the more data it can extract and the more damage it can do.
So here are just a few of the tactics that encryption malware employs to remain covert and maintain the anonymity of its makers and distributors:
- Communication with Command & Control servers is encrypted and difficult to detect in network traffic;
- It features built-in traffic anonymizers, like TOR and Bitcoin, to avoid tracking by law enforcement agencies and to receive ransom payments;
- It uses anti-sandboxing mechanisms so that antivirus won’t pick it up;
- It employs domain shadowing to conceal exploits and hide the communication between the downloader (payload) and the servers controlled by cyber criminals.
- It features Fast Flux, another technique used to keep the source of the infection anonymous;
- It deploys encrypted payloads which can make it more difficult for antivirus to see that they include malware, so the infection has more time to unfold;
- It has polymorphic behavior which gives it the ability to mutate enough to create a new variant, but not so much as to alter the malware’s function;
- It has the ability to remain dormant – the ransomware can remain inactive on the system until the computer is at its most vulnerable moment and take advantage of that to strike fast and effectively.


No comments:
Post a Comment